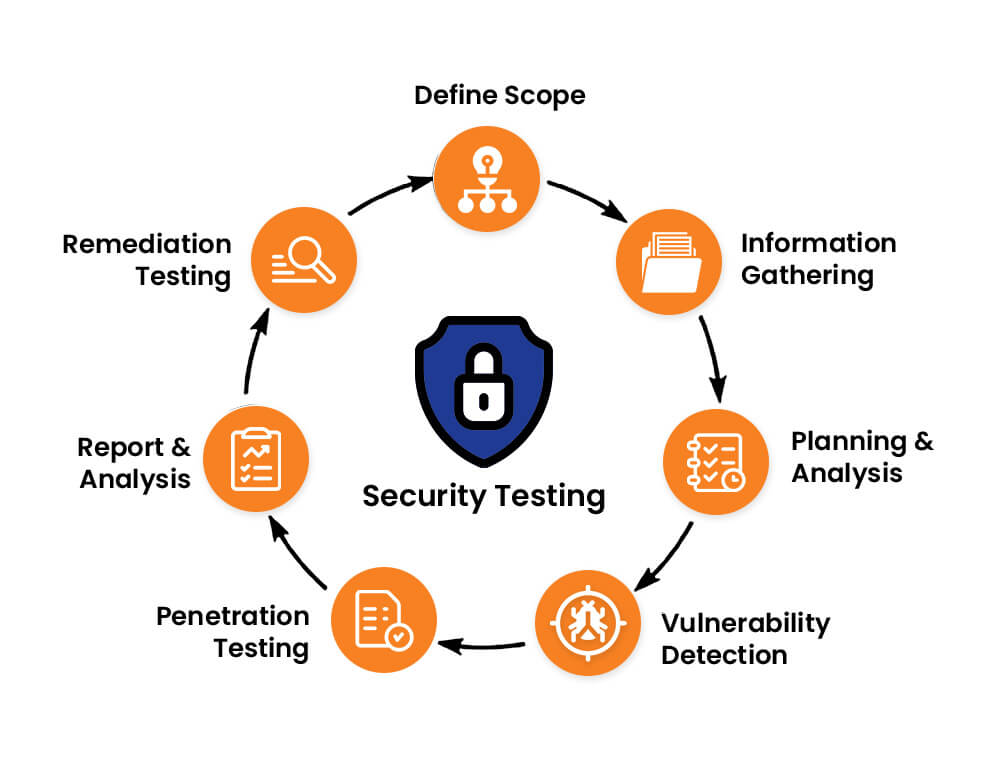
Comprehensive insights report
gain valuable insight into your security eco-system with detailed reports for strategic resource and business planning to safeguard your IT assets and future-proof your operational systems.
Protect customer loyalty and company image
even a single occurrence of compromised customer data can destroy a company’s brand and negatively impact its bottom line. Penetration testing helps an organization avoid data incidents that may put the company’s reputation and reliability at stake.

Convenience, schedule your vulnerability assessment anytime, anywhere.
Lorem Ipsum is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry's standard dummy text ever since the 1500s